BWSI Course - Embedded Security and Hardware Hacking
|
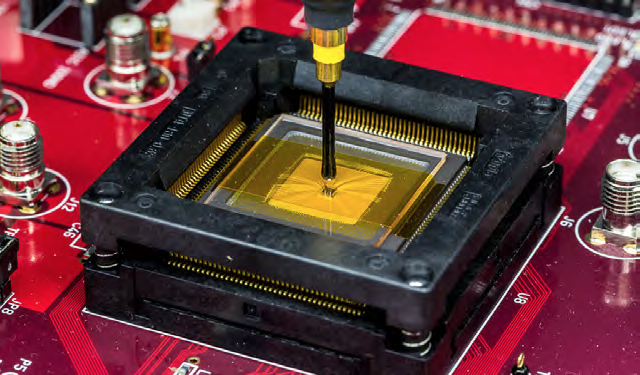
Most of us are aware of our reliance on computers throughout our everyday lives, but what we typically think of as computers (from the servers that run our favorite websites, to our laptops and smartphones) are only the tip of the iceberg. Hidden just beneath the surface is a substantial and diverse group of computers referred to as embedded systems. Although the concept may be unfamiliar to many, embedded systems are pervasive and have existed for decades. They commonly work within larger pieces of technology, performing specific tasks, such as operating one element of a car, medical device, aircraft, or even a musical instrument. Their security affects the security of the larger system. And they are being hacked! This program consists of two components: an online course from January to May open to all interested students and a four-week summer program from July 1 to August 1 for a select group of students. The online course will introduce the students to several security topics with a focus on threats that are especially concerning for embedded systems. These topics include: embedded software security, cryptographic protocol attacks, JTAG and UART probing, side-channel analysis and fault-injection, and hardware Trojans. This background will help prepare students for the summer course, during which they will perform security assessments of multiple implementations of an embedded system: a wireless home door lock. Teams will compete to see who can find and fix the most security flaws in these systems. Online CourseThe online component for the Embedded Security and hardware hacking course contains important introductory material to provide students with the background required to successfully complete the four-week summer course. A virtual machine image is provided for students to download and use on their own computers, with necessary tools preinstalled, so that they can work through both the introductory and more advanced topics. The online course will consist of the following modules:
Summer CourseThe four-week summer program is based on the MITRE Collegiate eCTF, which challenges teams of undergraduate and graduate students to design a secure system for an Internet-enabled home door lock with two-factor authentication. BWSI students will examine the submissions from real college teams and hunt for security flaws. The course will consist of a mix of lectures and hands-on projects that reinforce and apply the material. The detailed topics for each week are listed below: Week 1: Reconnaissance
Week 2: Cryptography and Security
Week 3: Hardware Analysis
Week 4: Hack!
|