Cyber Security Research Projects
The Beaver Works Cyber Security Center has a robust set of joint research projects in collaboration with MIT and other universities to challenge students to design, implement, test, and evaluate new systems and technology in cyber science and analysis, resilient cyber architectures, or secure embedded platforms.
Current Projects
LAREDO (Lincoln Automated Reverse Engineering and Dynamic Low-Observability) (2012 - Present)Lincoln Laboratory - Tim Leek Lincoln Laboratory’s LAREDO program aims to investigate and build novel tools and techniques to speed the current largely manual process of reverse engineering. This project would be impossible without Beaver Works, as it hinges on collaboration with top students and professors at Northeastern, Georgia Tech, and MIT. LAREDO funds a few students at Northeastern University, who have worked on a forensic disk analysis tool and an architecture-independent whole-system taint analysis. Under this program at Beaver Works, a student at Georgia Tech has made considerable advances in both application introspection and rehosting, two critical RE enablers. A student in the MIT Undergraduate Research Opportunities Program (UROP) has worked with us at Beaver Works on a novel trace-based decompilation idea. Beaver Works provides a critical space for these collaborations, in addition to housing shared computer servers to support them. |
|
Capture The Flag (CTF) (2012 - Present)Lincoln Laboratory - Tim Leek, Michael Zhivich Lincoln Laboratory runs an annual Cyber Capture the Flag Competition which is open to Boston-area colleges. 2013 was the third year for CTF and we had more than 150 students from 10 schools participate in this Android-themed game. They spent 40 hours without interruption working in teams of eight to defend Android apps and backend services while simultaneously trying to attack those of other teams. The purpose of this event is to promote interest and develop skills in Cyber Security and to select talented students for recruitment. It is funded in part by NSA's Laboratory for Telecommunications Science. The Lincoln Laboratory Director's Office funds prizes, T-shirts, and food for participants. In addition to the annual event, which is growing with each year, we also run several mini events in the same attack-defend format. These events are simpler, have much fewer challenges, last only a few hours, and are followed by presentation of solutions. Beaver Works is crucial to CTF. The computer infrastructure is housed there and development largely takes place there, often in collaboration with academics who provide challenges. The mini CTFs are also run at Beaver Works. |
|
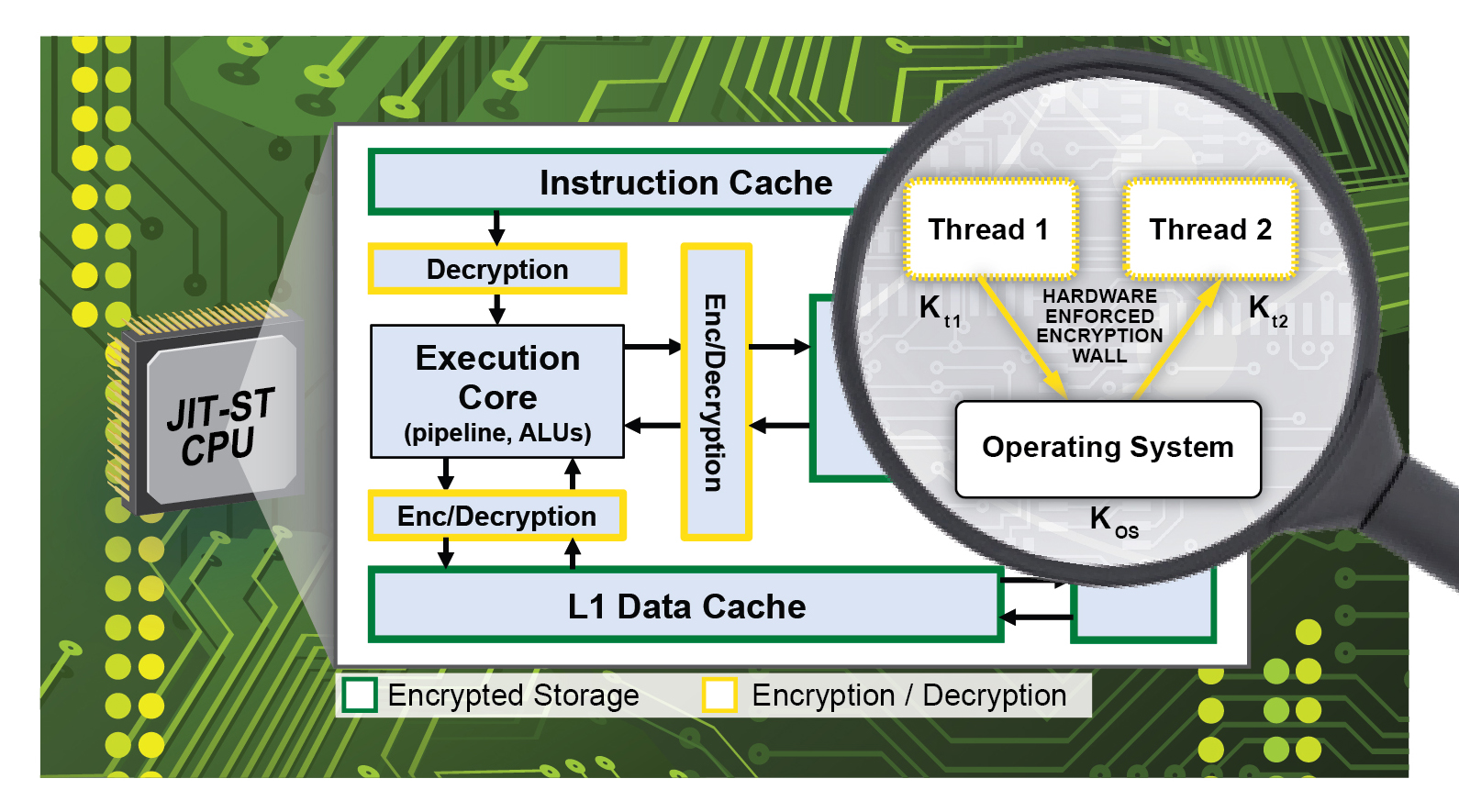
Trusted and Secure Computing (2013 - Present)Lincoln Laboratory - Brendon Chetwynd, David Whelihan, Paul Keltcher This collaboration is between Lincoln Laboratory and MIT CSAIL. The objective is to develop a trusted and secure computing architecture. The computer industry is currently faced with the challenge of protecting intellectual property, of which a large percentage is in computer code, from unauthorized access. Many current approaches depend on software-enforced process separation. However, issues arise due to the presence of privileged software (e.g., operating systems, hypervisors, etc.) that have unrestricted access to computing resources. Vulnerabilities in this privileged software coupled with malicious code exploiting them can result in an application gaining elevated privileges. Therefore, higher levels of system security should be supported by hardware extensions to provide enhanced process separation. We are working on fundamental research to develop solutions to issues in this important area. |
 |
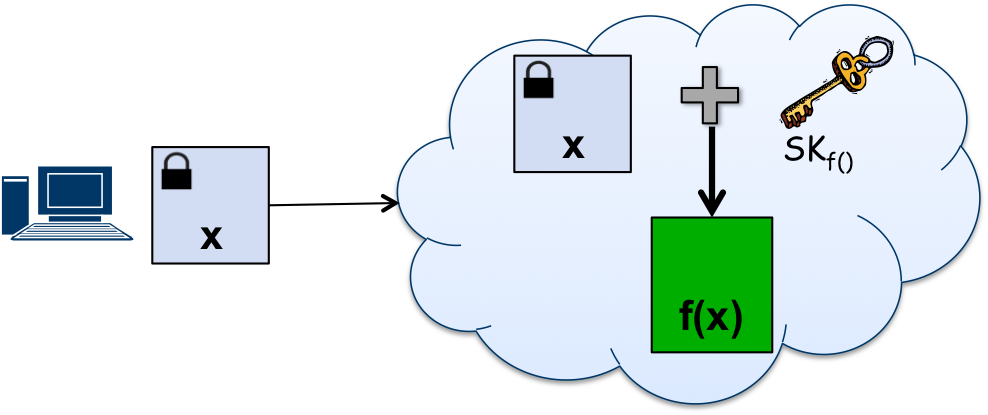
Functional Encryption (2013 - Present)Lincoln Laboratory - Arkady Yerukhimovich This collaboration is between Lincoln Laboratory and MIT CSAIL. In today’s environment, it is highly desirable to be able to outsource computation to a powerful computing cluster or cloud. However, current cloud computing solutions do not provide sufficient security of the data or computations performed. Functional encryption is a powerful tool that can help overcome these limitations. The collaboration objective is to further the state of the art in functional encryption, which allows finer control of encrypted data, and related primitives and to apply these primitives to security of cloud computing and other problems of interest. |
 |
Security Technologies of Protection Against Return-Oriented Programming (STOPROP) (2014 - Present)Lincoln Laboratory - Hamed Okhravi This collaboration is between Lincoln Laboratory and MIT CSAIL. The objective is to analyze and defend against a new, sophisticated form of cyber attack known as code reuse attacks (also known as return-oriented programming or ROP attacks). Code reuse attacks leverage the existing code from benign programs and libraries to perform a malicious behavior. Traditional systems security defenses against malicious code, such as code signing or trusted computing, are thus ineffective in stopping code reuse attacks. The objective of this research is to study code reuse attacks, analyze the effectiveness of the proposed defenses against them, and design and implement new, more effective defenses. The collaboration team includes three MIT EECS/Mechanical Engineering candidates, an MIT Undergraduate Advanced Projects student, CSAIL collaborators, and Lincoln Laboratory researchers. Beaver Works provides the crucial collaboration space for the team. |
|
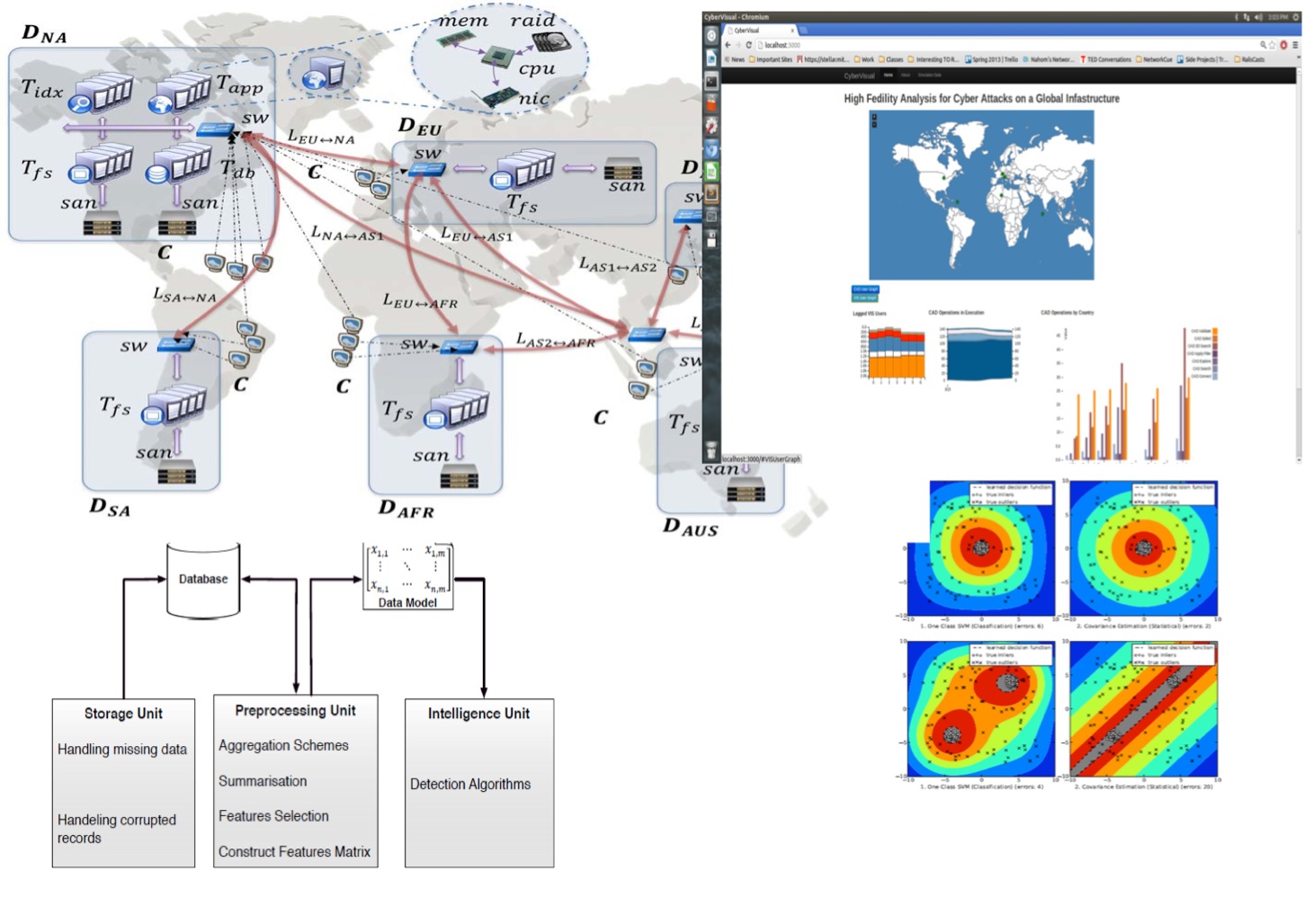
Repeatable Large System Impact Analysis (2012 - Present)Lincoln Laboratory - Suresh Damodaran In this project, we study how to perform repeatable cyber capacity tests and do the impact analysis of the tests for large globally networked enterprise systems. The goals are (1) to create high fidelity models of the systems so that the impacts of cyber attacks can be analyzed and(2) to explicitly model the tests and the enterprise systems for repeatability and portability of the tests and test results. |
 |